Zero Trust Security Market Analysis and Global Forecast 2023-2033
€ 1,230.43 – € 4,886.30Price range: € 1,230.43 through € 4,886.30
Global Zero Trust Security Market By Deployment Type (On-Premises, Cloud, Deployment Type 3), By Solution Type (Network Security, Data Security, Endpoint Security, API Security, Security Analytics, Others), By Authentication Type (Single-factor Authentication, Multi-factor Authentication), By Vertical Industry (IT and ITES, Financial and Insurance, Healthcare and Social Assistance, Retail Trade, Utilities, Others) and By Geography – COVID-19 Impact Analysis, Post COVID Analysis, Opportunities, Trends and Forecast from 2023 to 2033
Report Code: EB_ICT_357 | Page: 165| Published Date: March 2021
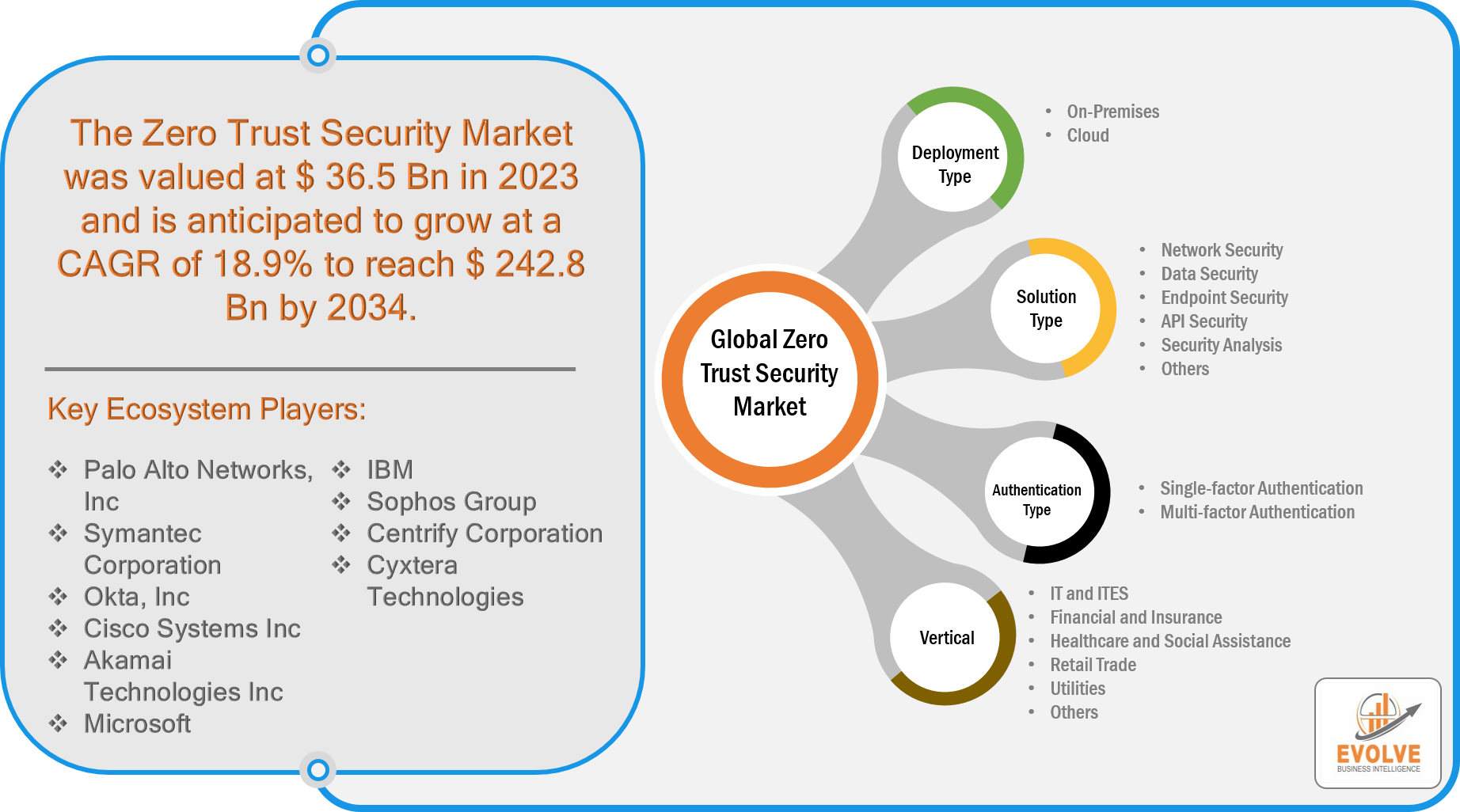
The Global Zero Trust Security Market size is projected to reach approximately $242.8 Billion by 2034, at a CAGR of 18.9% from 2024 to 2034. Zero Trust Security is a security model that assumes that all users, devices, and network traffic are potentially malicious and must be verified and authenticated before being granted access to resources. This model requires continuous authentication, authorization, and verification of all users and devices attempting to access resources, regardless of their location or network environment. In a Zero Trust Security model, access to resources is granted based on the user’s identity, the device they are using, the location they are accessing from, and other contextual information. This approach helps to prevent unauthorized access and reduces the risk of data breaches and cyber attacks by minimizing the attack surface and limiting the scope of potential threats. Zero Trust Security is becoming increasingly popular as businesses and organizations seek to protect their data and networks from cyber threats in an increasingly complex and interconnected digital environment.
COVID-19 Impact Analysis
the COVID-19 pandemic has had a positive impact on the Zero Trust Security market. With the shift to remote work and the increased reliance on cloud-based technologies, businesses, and organizations have become more vulnerable to cyber-attacks and data breaches. The Zero Trust Security model, which focuses on continuous authentication and authorization, is well-suited to address these challenges and provide enhanced security for remote workers and cloud-based Verticals.
 Zero Trust Security Market Dynamics
Zero Trust Security Market Dynamics
The driving factor of the zero trust security market is the increasing number of cyber threats, the adoption of cloud-based services, the increasing use of mobile devices, and remote working.
Drivers:
⮚ Rising numbers of Multi-factor Authentications
The rising number of Multi-factor Authentications (MFA) is expected to drive the growth of the Zero Trust Security market. MFA is a key component of Zero Trust Security, which is an approach to cybersecurity that assumes that all users, devices, and applications are potentially compromised and therefore requires strict authentication and access controls. MFA provides an extra layer of security by requiring users to provide two or more methods of authentication, such as a password and a fingerprint before they are granted access to a system or application. This helps to prevent unauthorized access to sensitive data and systems, even if a hacker manages to steal a user’s password. With the increasing number of cyber-attacks and data breaches, organizations are recognizing the importance of implementing stronger security measures such as MFA and Zero Trust Security. As a result, the demand for Zero Trust Security solutions that include MFA is expected to increase in the coming years.
Restraint:
- Lack of professionals to handle critical infrastructure
The lack of professionals to handle critical infrastructure is a potential restraint on the growth of the Zero Trust Security market. Critical infrastructure, such as power grids, transportation systems, and healthcare facilities, are essential for the functioning of society, and any disruption or cyber attack on these systems can have severe consequences. Implementing Zero Trust Security measures in critical infrastructure requires specialized skills and expertise in areas such as network security, identity and access management, and incident response. However, there is a shortage of professionals with these skills, making it challenging for organizations to implement and maintain robust Zero Trust Security solutions.
Opportunity:
⮚ Surging demand for cloud-based zero-trust security solutions among SMEs
SMEs often have limited resources and budgets for cybersecurity, making it challenging for them to implement and maintain robust security measures. However, with the increasing adoption of cloud-based services and remote work, SMEs are increasingly vulnerable to cyber threats and data breaches. Cloud-based Zero Trust Security solutions offer several benefits to SMEs, including cost-effectiveness, scalability, and ease of deployment and management. These solutions can provide SMEs with the same level of security as larger organizations without the need for extensive resources and expertise. As a result, there is a growing demand among SMEs for cloud-based Zero Trust Security solutions, creating an opportunity for vendors to market their solutions to this segment of the market.
Zero Trust Security Segment Overview
By Deployment Type
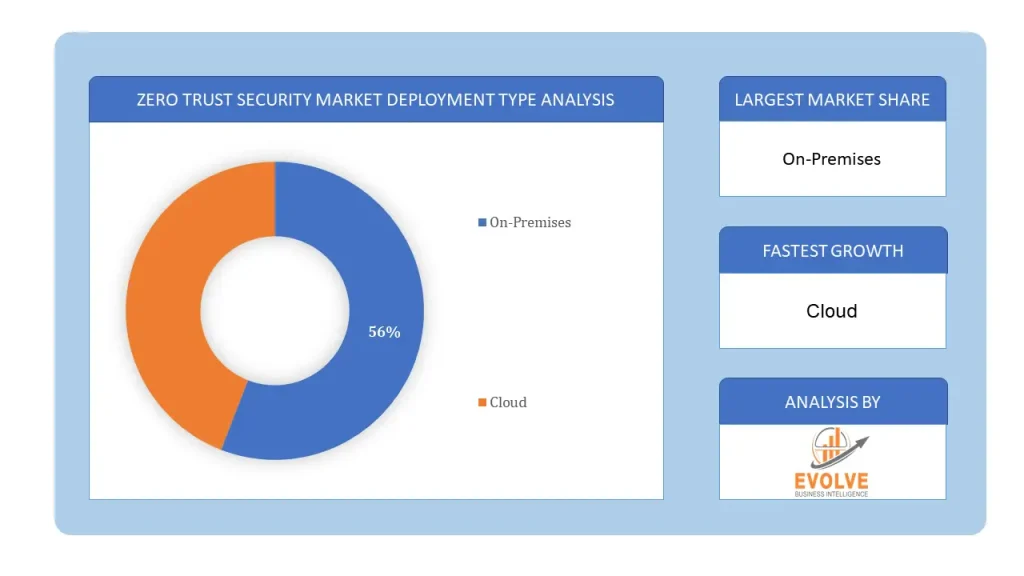 Based on the Deployment Type, the Zero Trust Security market is segmented based on On-Premises and Cloud. The Cloud segment is expected to hold the largest market share, This is due to the increasing adoption of cloud-based applications and services by businesses and organizations, which has resulted in the need for enhanced security measures to protect against cyber threats and data breaches.
Based on the Deployment Type, the Zero Trust Security market is segmented based on On-Premises and Cloud. The Cloud segment is expected to hold the largest market share, This is due to the increasing adoption of cloud-based applications and services by businesses and organizations, which has resulted in the need for enhanced security measures to protect against cyber threats and data breaches.
By Solution Type
Based on Solution Type, the global Zero Trust Security market has been divided into Network Security, Data Security, Endpoint Security, API Security, Security Analysis, and Others. The Data Security segment is expected to hold the largest market share. The increasing amount of sensitive data being generated and stored by businesses and organizations, combined with the growing number of data breaches and cyber attacks, has led to a greater focus on data security.
By Authentication Type
Based on Authentication Type, the global Zero Trust Security market has been divided into Single-factor Authentication and Multi-factor Authentication. The demolition segment is expected to hold the largest market share. The growing number of cyber threats and data breaches has led to an increased focus on MFA as a means of enhancing security for businesses and organizations. This is especially true in industries such as finance, healthcare, and government, where sensitive data is often stored and transmitted.
By Vertical
Based on Vertical, the global Zero Trust Security market has been divided into IT and ITES, Financial and Insurance, Healthcare and Social Assistance, Retail Trade, Utilities, and Others. The IT and ITES segment holds the largest market share of Zero Trust Security. The IT and ITES industry is one of the largest consumers of digital technology and cloud-based services, which makes it particularly vulnerable to cyber threats and data breaches. Therefore, businesses in this industry have a higher need for strong security measures, including Zero Trust Security, to protect their sensitive data and systems.
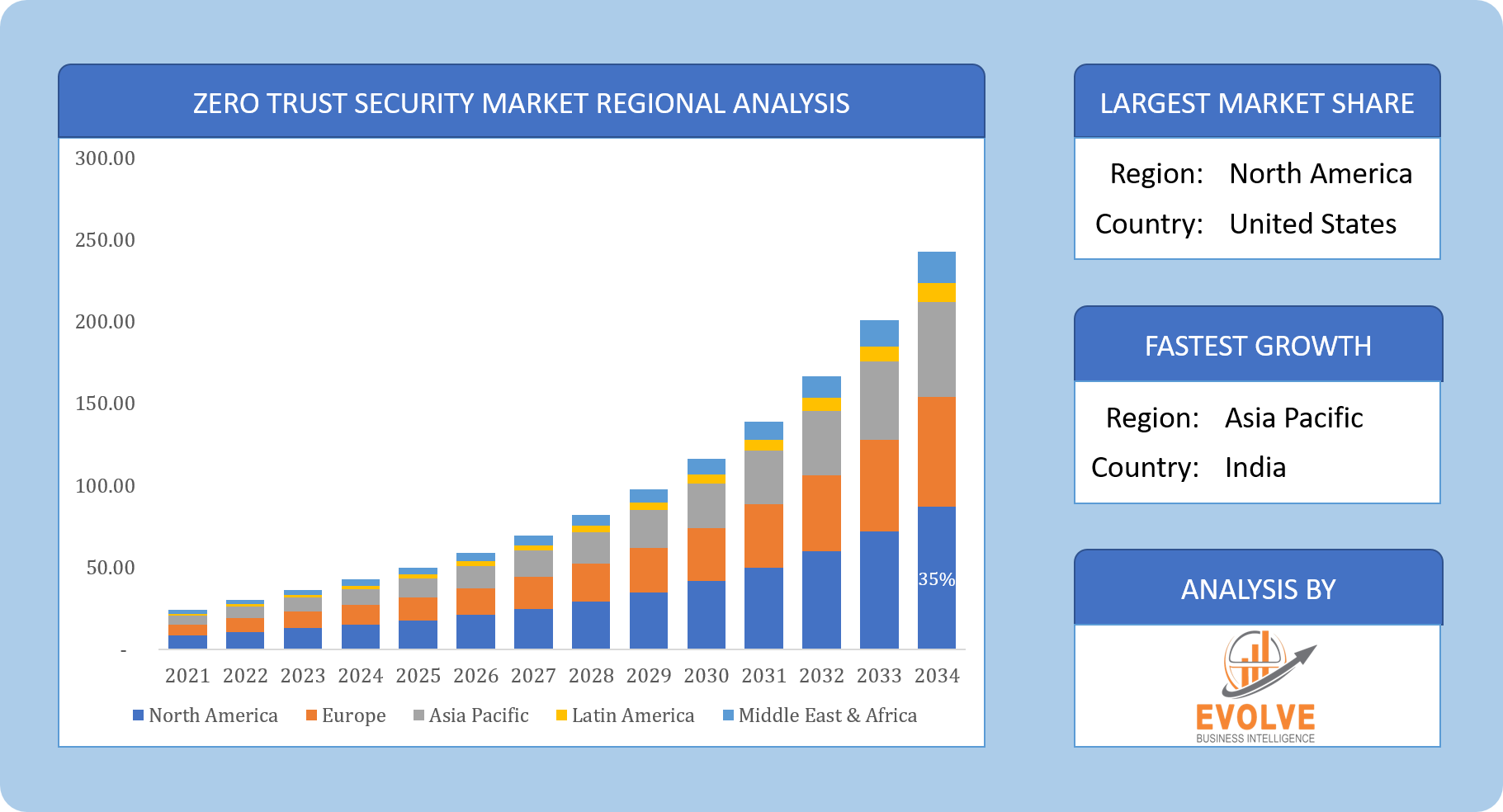
Global Zero Trust Security Market Share, by Region
 Zero Trust Security Regional Analysis
Zero Trust Security Regional Analysis
Based on region, the global Zero Trust Security market has been divided into North America, Europe, Asia-Pacific, and the Rest of the World. North America is projected to dominate the use of the Zero Trust Security market followed by the Asia-Pacific and Europe regions.
North America Market
North America is one of the dominant regions in the global zero-trust security market. The region has a well-developed cybersecurity industry and is home to many of the leading providers of Zero Trust Security solutions, including Cisco Systems, Microsoft Corporation, Okta Inc., and Palo Alto Networks Inc. The U.S., in particular, has been a major market for Zero Trust Security solutions, driven by the increasing number of cyber threats and data breaches affecting businesses and government agencies. The U.S. government has also played a significant role in promoting the adoption of Zero Trust Security through initiatives such as the Cybersecurity and Infrastructure Security Agency’s (CISA) Zero Trust Architecture guidelines.
Asia-Pacific Market
The Asia-Pacific region has one of the fastest-growing CAGR in the Zero Trust Security market. The increasing adoption of cloud-based technologies, the growing number of cyber threats, and the increasing regulatory compliance requirements are driving the demand for Zero Trust Security solutions in the region. Several countries in the Asia-Pacific region, including China, India, Japan, and Australia, have made significant investments in cybersecurity infrastructure in recent years, which has contributed to the growth of the Zero Trust Security market. Additionally, the increasing number of small and medium-sized businesses in the region is also driving the demand for cost-effective and scalable Zero Trust Security solutions.
Competitive Landscape
The market comprises tier-1, tier-2, and local players. With their wide product portfolios, tier-1 and tier-2 players have a global reach. Since of their strategic innovations and broad regional presence, companies such as Cisco Systems Inc, Akamai Technologies Inc, Microsoft, and IBM lead the zero trust security market. To increase their market position and attract a wide consumer base, the businesses are employing various strategies, such as growth, product releases, and alliances.
Prominent Players:
- Palo Alto Networks, Inc
- Symantec Corporation
- Okta, Inc
- Cisco Systems Inc
- Akamai Technologies Inc
- Microsoft
- IBM
- Sophos Group
- Centrify Corporation
- Cyxtera Technologies
Scope of the Report
Global Zero Trust Security Market, by Deployment Type
- On-Premises
- Cloud
Global Zero Trust Security Market, by Solution Type
- Network Security
- Data Security
- Endpoint Security
- API Security
- Security Analysis
- Others
Global Zero Trust Security Market, by Authentication Type
- Single-factor Authentication
- Multi-factor Authentication
Global Zero Trust Security Market, by Vertical
- IT and ITES
- Financial and Insurance
- Healthcare and Social Assistance
- Retail Trade
- Utilities
- Others
Global Zero Trust Security Market, by Region
- North America
- US
- Canada
- Mexico
- Europe
- UK
- Germany
- France
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Rest of Asia Pacific
- Rest of the World
| Parameters | Indicators |
|---|---|
| Market Size | 2034: $ 242.8 Billion |
| CAGR | 18.9% CAGR (2024-2034) |
| Base year | 2023 |
| Forecast Period | 2024-2034 |
| Historical Data | 2022 |
| Report Coverage | Revenue Forecast, Competitive Landscape, Growth Factors, and Trends |
| Key Segmentations | Deployment Type, Solution Type, Authentication Type, Vertical |
| Geographies Covered | North America, Europe, Asia-Pacific, Latin America, Middle East, Africa |
| Key Vendors | Palo Alto Networks, Inc, Symantec Corporation, Okta Inc, Cisco Systems Inc, Akamai Technologies Inc, Microsoft, IBM, Sophos Group, Centrify Corporation, Cyxtera Technologies |
| Key Market Opportunities | Surging demand for cloud-based zero-trust security solutions among SMEs |
| Key Market Drivers | Rising numbers of Multi-factor Authentications |
REPORT CONTENT BRIEF:
- High-level analysis of the current and future Zero Trust Security market trends and opportunities
- Detailed analysis of current market drivers, restraining factors, and opportunities in the future
- Zero Trust Security market historical market size for the year 2022, and forecast from 2024 to 2034
- Zero Trust Security market share analysis at each product level
- Competitor analysis with a detailed insight into its product segment, financial strength, and strategies adopted.
- Identifies key strategies adopted including product launches and developments, mergers and acquisitions, joint ventures, collaborations, and partnerships as well as funding taken and investment done, among others.
- To identify and understand the various factors involved in the global Zero Trust Security market affected by the pandemic
- To provide a detailed insight into the major companies operating in the market. The profiling will include the financial health of the company’s past 2-3 years with segmental and regional revenue breakup, product offering, recent developments, SWOT analysis, and key strategies.
Press Release

Global Pharmaceutical Manufacturing Market to Reach $1.38 Trillion by 2035 with 7.35% CAGR, New Research Shows

The Global Mammography Market Is Estimated To Record a CAGR of Around 10.29% During The Forecast Period

Glue Stick Market to Reach USD 2.35 Billion by 2034

Podiatry Service Market to Reach USD 11.88 Billion by 2034

Microfluidics Technology Market to Reach USD 32.58 Billion by 2034

Ferric Chloride Market to Reach USD 10.65 Billion by 2034

Family Practice EMR Software Market to Reach USD 21.52 Billion by 2034

Electric Hairbrush Market to Reach USD 15.95 Billion by 2034

Daily Bamboo Products Market to Reach USD 143.52 Billion by 2034

Cross-border E-commerce Logistics Market to Reach USD 112.65 Billion by 2034
Frequently Asked Questions (FAQ)
What is the study period of this market?
The study period of the global Zero Trust Security market is 2022- 2033
What is the growth rate of the global Zero Trust Security market?
The global Zero Trust Security market is growing at a CAGR of ~ 18.21% over the next 10 years
Which region has the highest growth rate in the global Zero Trust Security market?
Asia-Pacific is expected to register the highest CAGR during 2022-2033
Which region has the largest share in the global Zero Trust Security market?
North America holds the largest share in 2022
Who are the key players in the global Zero Trust Security market?
Palo Alto Networks, Inc, Symantec Corporation, Okta Inc, Cisco Systems Inc, Akamai Technologies Inc, Microsoft, IBM, Sophos Group, Centrify Corporation, and Cyxtera Technologies are the major companies operating in the global Zero Trust Security market.
Do you offer Post Sale Support?
Yes, we offer 16 hours of analyst support to solve the queries
Do you sell particular sections of a report?
Yes, we provide regional as well as country-level reports. Other than this we also provide a sectional report. Please get in contact with our sales representatives.
Table of Content
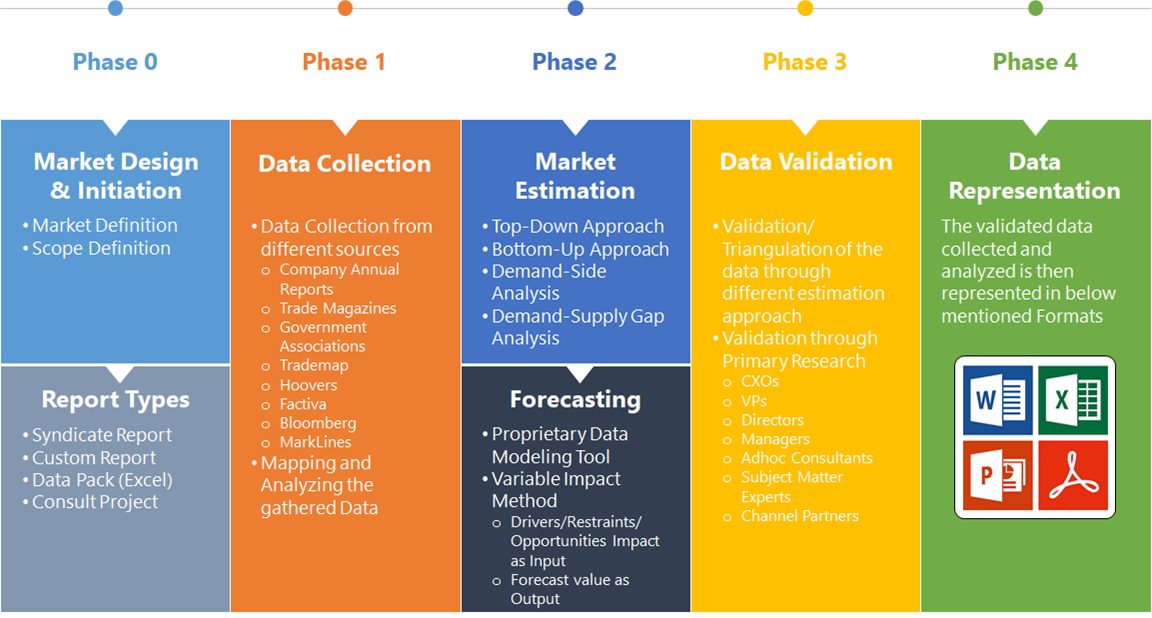
Chapter 1. Executive Summary Chapter 2. Scope Of The Study 2.1. Market Definition 2.2. Scope Of The Study 2.2.1. Objectives of Report Chapter 3. Evolve BI Methodology Chapter 4. Market Insights and Trends 4.1. Supply/ Value Chain Analysis 4.2. Porter’s Five Forces Analysis 4.2.1. Threat Of New Entrants 4.2.2. Bargaining Power Of Buyers 4.2.3. Bargaining Power Of Suppliers 4.2.4. Threat Of Substitutes 4.2.5. Industry Rivalry 4.3. Impact of COVID-19 on Zero Trust Security Market 4.3.1. Impact on Market Size 4.3.2. Vertical Industry Trend, Preferences and Budget Impact 4.3.3. Regulatory Framework/Government Policies 4.3.4. Key Players Strategy to Tackle Negative Impact 4.3.5. Opportunity Window Chapter 5. Market Dynamics 5.1. Introduction 5.2. DRO Analysis 5.2.1. Drivers 5.2.2. Restraints 5.2.3. Opportunities Chapter 6. Global Zero Trust Security Market, By Deployment Type 6.1. Introduction 6.2. On-Premises 6.3. Cloud Chapter 7. Global Zero Trust Security Market, By Solution Type 7.1. Introduction 7.2. Network Security 7.3. Data Security 7.4. Endpoint Security 7.5. API Security 7.6. Security Analysis 7.7. Others Chapter 8. Global Zero Trust Security Market, By Authentication Type 8.1. Introduction 8.2. Single-factor Authentication 8.3. Multi-factor Authentication Chapter 9. Global Zero Trust Security Market, By Vertical Industry 9.1. Introduction 9.2. IT and ITES 9.3. Financial and Insurance 9.4. Healthcare and Social Assistance 9.5. Retail Trade 9.6. Utilities 9.7. Others Chapter 10. Global Zero Trust Security Market, By Region 10.1. Introduction 10.2. North America 10.2.1. Introduction 10.2.2. Driving Factors, Opportunity Analyzed and Key Trends 10.2.3. Market Size and Forecast, By Country, 2020 - 2028 10.2.4. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.2.5. Market Size and Forecast, By Solution Type, 2020 - 2028 10.2.6. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.2.7. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.2.8. US 10.2.8.1. Introduction 10.2.8.2. Driving Factors, Opportunity Analyzed and Key Trends 10.2.8.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.2.8.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.2.8.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.2.8.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.2.9. Canada 10.2.9.1. Introduction 10.2.9.2. Driving Factors, Opportunity Analyzed and Key Trends 10.2.9.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.2.9.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.2.9.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.2.9.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.3. Europe 10.3.1. Introduction 10.3.2. Driving Factors, Opportunity Analyzed and Key Trends 10.3.3. Market Size and Forecast, By Country, 2020 - 2028 10.3.4. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.3.5. Market Size and Forecast, By Solution Type, 2020 - 2028 10.3.6. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.3.7. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.3.8. Germany 10.3.8.1. Introduction 10.3.8.2. Driving Factors, Opportunity Analyzed and Key Trends 10.3.8.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.3.8.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.3.8.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.3.8.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.3.9. France 10.3.9.1. Introduction 10.3.9.2. Driving Factors, Opportunity Analyzed and Key Trends 10.3.9.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.3.9.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.3.9.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.3.9.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.3.10. UK 10.3.10.1. Introduction 10.3.10.2. Driving Factors, Opportunity Analyzed and Key Trends 10.3.10.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.3.10.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.3.10.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.3.10.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.3.11. Italy 10.3.11.1. Introduction 10.3.11.2. Driving Factors, Opportunity Analyzed and Key Trends 10.3.11.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.3.11.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.3.11.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.3.11.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.3.12. Rest Of Europe 10.3.12.1. Introduction 10.3.12.2. Driving Factors, Opportunity Analyzed and Key Trends 10.3.12.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.3.12.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.3.12.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.3.12.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.4. Asia-Pacific 10.4.1. Introduction 10.4.2. Driving Factors, Opportunity Analyzed and Key Trends 10.4.3. Market Size and Forecast, By Country, 2020 - 2028 10.4.4. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.4.5. Market Size and Forecast, By Solution Type, 2020 - 2028 10.4.6. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.4.7. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.4.8. China 10.4.8.1. Introduction 10.4.8.2. Driving Factors, Opportunity Analyzed and Key Trends 10.4.8.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.4.8.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.4.8.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.4.8.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.4.9. India 10.4.9.1. Introduction 10.4.9.2. Driving Factors, Opportunity Analyzed and Key Trends 10.4.9.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.4.9.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.4.9.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.4.9.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.4.10. Japan 10.4.10.1. Introduction 10.4.10.2. Driving Factors, Opportunity Analyzed and Key Trends 10.4.10.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.4.10.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.4.10.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.4.10.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.4.11. South Korea 10.4.11.1. Introduction 10.4.11.2. Driving Factors, Opportunity Analyzed and Key Trends 10.4.11.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.4.11.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.4.11.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.4.11.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.4.12. Rest Of Asia-Pacific 10.4.12.1. Introduction 10.4.12.2. Driving Factors, Opportunity Analyzed and Key Trends 10.4.12.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.4.12.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.4.12.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.4.12.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.5. Rest Of The World (RoW) 10.5.1. Introduction 10.5.2. Driving Factors, Opportunity Analyzed and Key Trends 10.5.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.5.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.5.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.5.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.5.7. Market Size and Forecast, By Region, 2020 - 2028 10.5.8. South America 10.5.8.1. Introduction 10.5.8.2. Driving Factors, Opportunity Analyzed and Key Trends 10.5.8.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.5.8.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.5.8.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.5.8.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 10.5.9. Middle East & Afirica 10.5.9.1. Introduction 10.5.9.2. Driving Factors, Opportunity Analyzed and Key Trends 10.5.9.3. Market Size and Forecast, By Deployment Type, 2020 - 2028 10.5.9.4. Market Size and Forecast, By Solution Type, 2020 - 2028 10.5.9.5. Market Size and Forecast, By Authentication Type, 2020 - 2028 10.5.9.6. Market Size and Forecast, By Vertical Industry, 2020 - 2028 Chapter 11. Competitive Landscape 11.1. Introduction 11.2. Vendor Share Analysis, 2020/Key Players Positioning, 2020 Chapter 12. Company Profiles 12.1. Palo Alto Networks, Inc. 12.1.1. Business Overview 12.1.2. Financial Analysis 12.1.3. Product Portfolio 12.1.4. Recent Development and Strategies Adopted 12.1.5. SWOT Analysis 12.2. Symantec Corporation 12.2.1. Business Overview 12.2.2. Financial Analysis 12.2.3. Product Portfolio 12.2.4. Recent Development and Strategies Adopted 12.2.5. SWOT Analysis 12.3. Okta, Inc. 12.3.1. Business Overview 12.3.2. Financial Analysis 12.3.3. Product Portfolio 12.3.4. Recent Development and Strategies Adopted 12.3.5. SWOT Analysis 12.4. Cisco Systems Inc. 12.4.1. Business Overview 12.4.2. Financial Analysis 12.4.3. Product Portfolio 12.4.4. Recent Development and Strategies Adopted 12.4.5. SWOT Analysis 12.5. Akamai Technologies, Inc. 12.5.1. Business Overview 12.5.2. Financial Analysis 12.5.3. Product Portfolio 12.5.4. Recent Development and Strategies Adopted 12.5.5. SWOT Analysis 12.6. Microsoft 12.6.1. Business Overview 12.6.2. Financial Analysis 12.6.3. Product Portfolio 12.6.4. Recent Development and Strategies Adopted 12.6.5. SWOT Analysis 12.7. IBM 12.7.1. Business Overview 12.7.2. Financial Analysis 12.7.3. Product Portfolio 12.7.4. Recent Development and Strategies Adopted 12.7.5. SWOT Analysis 12.8. Sophos Group 12.8.1. Business Overview 12.8.2. Financial Analysis 12.8.3. Product Portfolio 12.8.4. Recent Development and Strategies Adopted 12.8.5. SWOT Analysis 12.9. Centrify Corporation 12.9.1. Business Overview 12.9.2. Financial Analysis 12.9.3. Product Portfolio 12.9.4. Recent Development and Strategies Adopted 12.9.5. SWOT Analysis 12.10. Cyxtera Technologies 12.10.1. Business Overview 12.10.2. Financial Analysis 12.10.3. Product Portfolio 12.10.4. Recent Development and Strategies Adopted 12.10.5. SWOT Analysis Chapter 13. Key Takeaways
Connect to Analyst
Research Methodology