Multi-Factor Authentication Market Overview
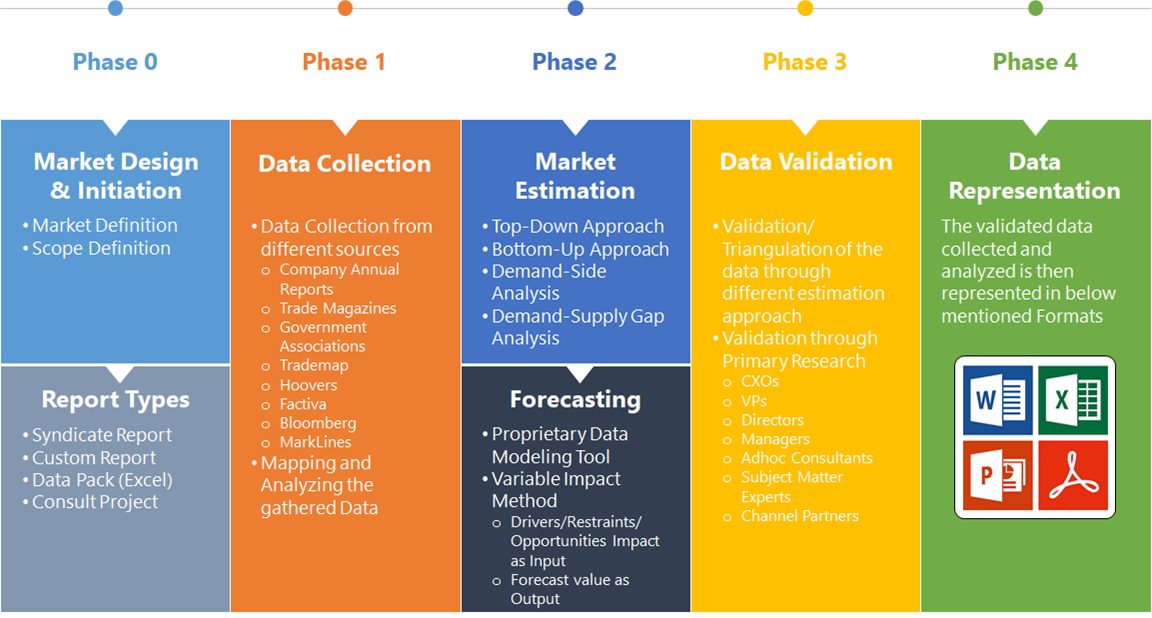
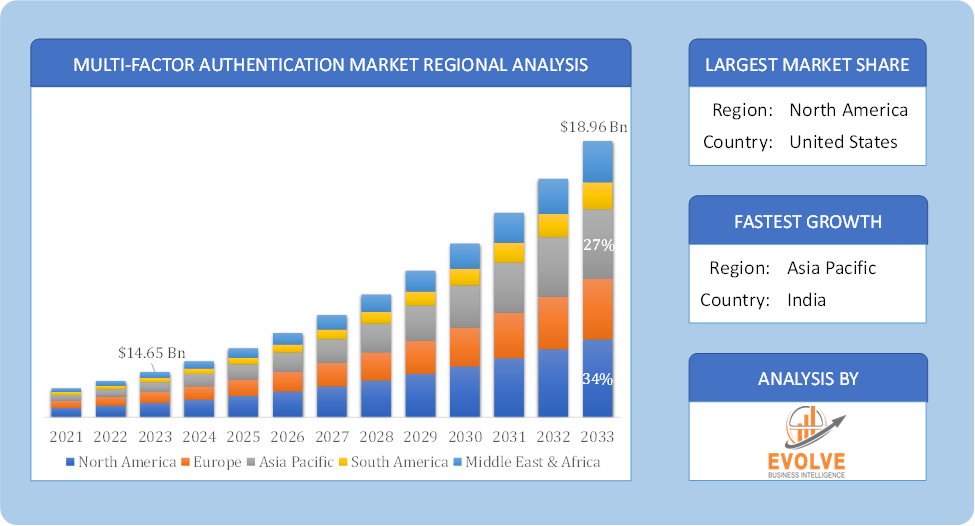
The Multi-Factor Authentication Market Size is expected to reach USD 18.96 Billion by 2033. The Multi-Factor Authentication industry size accounted for USD 14.65 Billion in 2023 and is expected to expand at a compound annual growth rate (CAGR) of 6.5% from 2023 to 2033. The Multi-Factor Authentication (MFA) market focuses on technologies and solutions designed to enhance security by requiring users to provide two or more verification factors to gain access to a system, application, or data. MFA typically combines something the user knows (like a password), something the user has (such as a smartphone or security token), and something the user is (biometric identifiers). The market is driven by increasing cybersecurity threats, regulatory compliance requirements, and the growing adoption of digital transformation. Key segments include hardware tokens, software tokens, and biometric solutions. Major players in the market are constantly innovating to improve user experience and security.
Global Multi-Factor Authentication Market Synopsis
 COVID-19 Impact Analysis
COVID-19 Impact Analysis
The COVID-19 pandemic has led to supply chain disruptions leading to supply shortages or lower demand in the Multi-Factor Authentication market. The travel restrictions and social-distancing measures have resulted in a sharp drop in consumer and business spending and this pattern is to continue for some time. The end-user trend and preferences have changed due to the pandemic and have resulted in manufacturers, developers, and service providers to adopt various strategies to stabilize the company.
Multi-Factor Authentication Market Dynamics
The major factors that have impacted the growth of Multi-Factor Authentication are as follows:
Drivers:
Ø Digital Transformation
As organizations migrate to digital platforms and cloud-based services, the need for secure authentication methods has grown. MFA provides an essential security measure for accessing cloud applications, remote work environments, and online services, supporting the broader digital transformation efforts.
Restraint:
- Technical Limitations and Vulnerabilities
While MFA enhances security, it is not immune to technical vulnerabilities. For example, SMS-based authentication can be susceptible to interception and SIM swapping attacks. Biometric systems can face accuracy and spoofing issues. These limitations can impact the overall security and effectiveness of MFA solutions.
Opportunity:
⮚ Technological Innovations
Advances in biometric technologies, such as facial recognition, fingerprint scanning, and voice recognition, offer new opportunities for enhancing MFA solutions. Innovations in behavioral biometrics and machine learning can further improve the accuracy and user experience of MFA systems, making them more effective and appealing.
Multi-Factor Authentication Segment Overview
 By Authentication
By Authentication
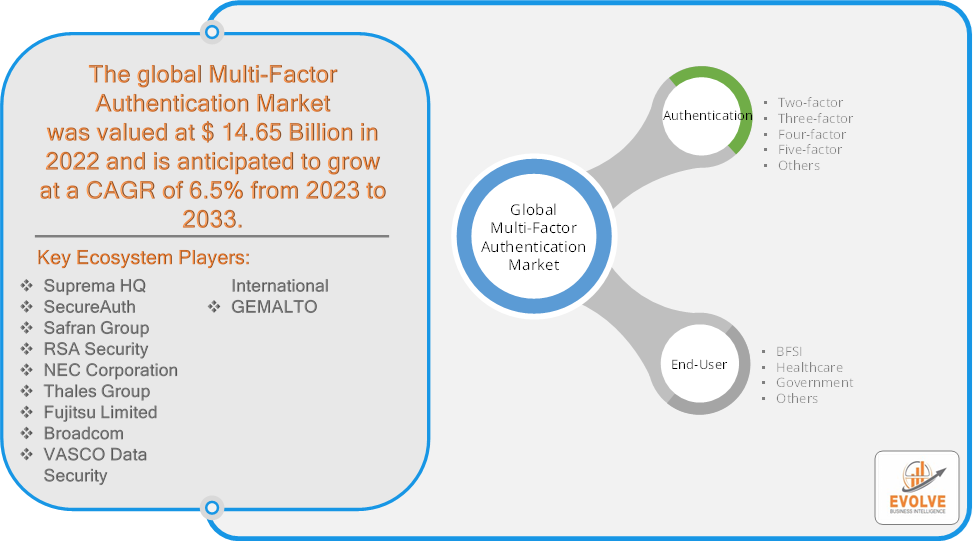
Based on Authentication, the market is segmented based on Two-factor, Three-factor, Four-factor, Five-factor. the Two-Factor Authentication (2FA) segment dominates due to its balance of enhanced security and user convenience, making it the most widely adopted method across various applications and industries.
By End User
Based on End Users, the market has been divided into the BFSI, Healthcare, Government, Others. the BFSI (Banking, Financial Services, and Insurance) sector dominates due to its high demand for robust security measures to protect sensitive financial data and comply with stringent regulatory requirements.
Global Multi-Factor Authentication Market Regional Analysis
Based on region, the global Multi-Factor Authentication market has been divided into North America, Europe, Asia-Pacific, the Middle East & Africa, and Latin America. North America is projected to dominate the use of the Multi-Factor Authentication market followed by the Asia-Pacific and Europe regions.
 Multi-Factor Authentication North America Market
Multi-Factor Authentication North America Market
North America holds a dominant position in the Multi-Factor Authentication Market. Consumers losing hundreds of dollars to online fraudsters and the surge in data theft are the main reasons behind North America’s multifactor authentication marketers of large identity crimes. Furthermore, the North American industry will gain from the presence of important actors and consumers in the United States, such as banks and large healthcare providers.
Multi-Factor Authentication Asia-Pacific Market
The Asia-Pacific region has indeed emerged as the fastest-growing market for the Multi-Factor Authentication industry. From 2023 to 2030, the Asia-Pacific Multifactor Authentication Market is anticipated to expand at the fastest rate. Major Asian banks now have access to CREALOGIX’s service, which offers users a single application for both identity verification and banking. As part of a multi-factor authentication system, hardware devices no longer produce hardware tokens for one-time passwords (OTPs) for every operation. With soft tokens, all the security advantages of multifactor authentication are available in place of hard tokens.
Competitive Landscape
The global Multi-Factor Authentication market is highly competitive, with numerous players offering a wide range of software solutions. The competitive landscape is characterized by the presence of established companies, as well as emerging startups and niche players. To increase their market position and attract a wide consumer base, the businesses are employing various strategies, such as Authenticationlaunches, and strategic alliances.
Prominent Players:
- Suprema HQ
- SecureAuth
- Safran Group
- RSA Security
- NEC Corporation
- Thales Group
- Fujitsu Limited
- Broadcom
- VASCO Data Security International
- GEMALTO
Key Development
In September 2022, NEC Corporation enhanced its Multi-Factor Authentication (MFA) capabilities by introducing advanced biometric authentication solutions, including facial and fingerprint recognition, to bolster security and streamline user access in its IAM solutions.
Scope of the Report
Global Multi-Factor Authentication Market, by Authentication
- Two-factor
- Three-factor
- Four-factor
- Five-factor
- Others
Global Multi-Factor Authentication Market, by End-User
- BFSI
- Healthcare
- Government
- Others
Global Multi-Factor Authentication Market, by Region
- North America
- US
- Canada
- Mexico
- Europe
- UK
- Germany
- France
- Italy
- Spain
- Benelux
- Nordic
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- Indonesia
- Austalia
- Malaysia
- India
- Rest of Asia Pacific
- South America
- Brazil
- Argentina
- Rest of South America
- Middle East & Africa
- Saudi Arabia
- UAE
- Egypt
- South Africa
- Rest of Middle East & Africa
| Parameters | Indicators |
|---|---|
| Market Size | 2033: USD 18.96 Billion |
| CAGR (2023-2033) | 6.5% |
| Base year | 2022 |
| Forecast Period | 2023-2033 |
| Historical Data | 2021 (2017 to 2020 On Demand) |
| Report Coverage | Revenue Forecast, Competitive Landscape, Growth Factors, and Trends |
| Key Segmentations | Authentication, End User |
| Geographies Covered | North America, Europe, Asia-Pacific, South America, Middle East, Africa |
| Key Vendors | Suprema HQ, SecureAuth, Safran Group, RSA Security, NEC Corporation, Thales Group, Fujitsu Limited, Broadcom, VASCO Data Security International, GEMALTO. |
| Key Market Opportunities | · Rising adoption of interconnected devices in the IoT environment. |
| Key Market Drivers | · Growing adoption of BYOD, CYOD and WFH trends. Rising security breaches and sophisticated cyberattacks lead to financial and reputational loss |
REPORT CONTENT BRIEF:
- High-level analysis of the current and future Multi-Factor Authentication market trends and opportunities
- Detailed analysis of current market drivers, restraining factors, and opportunities in the future
- Multi-Factor Authentication market historical market size for the year 2021, and forecast from 2023 to 2033
- Multi-Factor Authentication market share analysis at each Authentication level
- Competitor analysis with detailed insight into its Authentication segment, Government & Defense strength, and strategies adopted.
- Identifies key strategies adopted including Authentication launches and developments, mergers and acquisitions, joint ventures, collaborations, and partnerships as well as funding taken and investment done, among others.
- To identify and understand the various factors involved in the global Multi-Factor Authentication market affected by the pandemic
- To provide a detailed insight into the major companies operating in the market. The profiling will include the Government & Defense health of the company’s past 2-3 years with segmental and regional revenue breakup, Authentication offering, recent developments, SWOT analysis, and key strategies.